
Anatomy of the attack
In 2019, the Australian National University in Canberra disclosed that they had been breached by a sophisticated threat actor. They were active in the network for five months between November 2018 and March 2019. The threat actor exfiltrated sensitive personal staff, student and visitor data extending back 19 years however, the exact data that was taken is unknown due to the high degree of operational security employed and the fact that to date the data hasn’t been released online.
There is a strong potential that the sensitive information gathered in this attack included the personal information of former students who had then attained high-level roles in the Australian government including many prime ministers and diplomats.
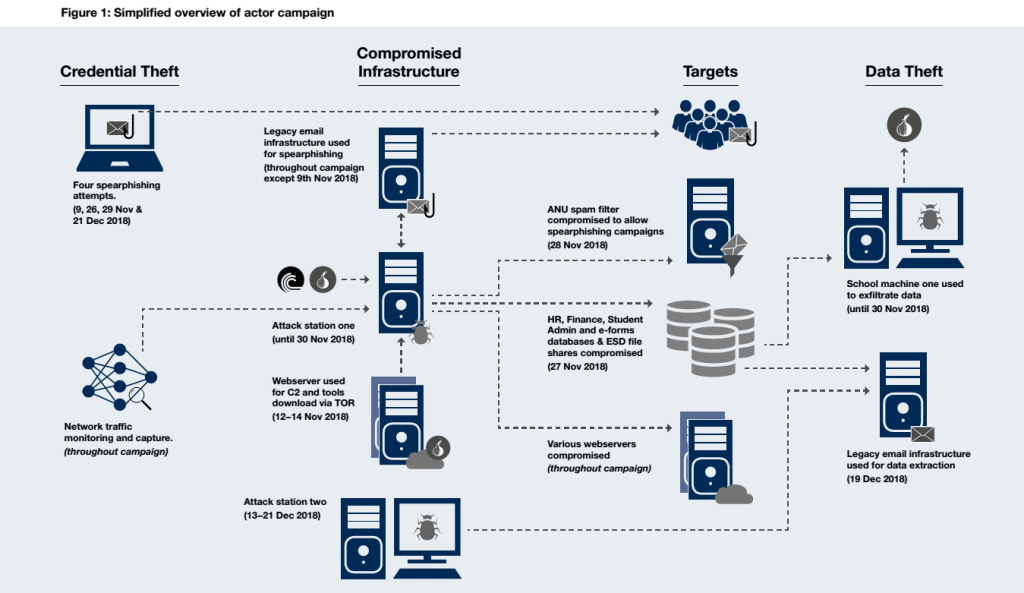
The hacking campaign unfolded through a series of meticulously orchestrated spearphishing attacks, where the threat actor successfully targeted a senior staff member, obtaining their credentials. This initial breach served as a gateway for the attacker to compromise critical infrastructure and establish a foothold within the network. To bolster the credibility of subsequent spearphishing attacks, the threat actor also gained access to the senior staff member’s calendar.
Having acquired the first set of credentials, the actor proceeded to compromise an internet-facing web server. Using this compromised entry point, they skillfully pivoted to gain control over a legacy server, which was connected via VLAN to a substantial portion of the ANU network.
The subsequent steps in the attack involved the creation of virtual machines on the compromised legacy server and the connection to a legacy mail server lacking authentication. From there, the actor sent out emails likely containing sensitive data related to network mapping, user information, and machine data. Additionally, the threat actor established a tunnelling proxy, initiated packet captures, and executed a second set of spearphishing emails, resulting in the acquisition of a single credential that was promptly utilised.
Buoyed by their success, the actor intensified their campaign, attempting to compromise a range of servers using a combination of exploits and stolen credentials. A bespoke toolset was downloaded and employed for password cracking, facilitating access to the Enterprise Systems Domain file (ESD). This file contained critical data encompassing human resources, financial management, student administration, and enterprise information. Using a commercial tool, the attacker accessed databases, searched for records, converted them to PDF format, and extracted the data.
The campaign persisted with the initiation of another round of spearphishing emails, yielding an administrator credential. However, the threat actor’s activities were disrupted by a routine firewall change, leading to the termination of their attack station. Undeterred, the actor sought to regain access to the station and concurrently secure another foothold within the network.
Access to the network was restored by compromising a machine running a legacy operating system, positioned outside the university firewalls and featuring a publicly routable IP address. During this phase, the threat actor exfiltrated an additional 13 files, further expanding their reach. Subsequently, a fourth spearphishing phase commenced, successfully acquiring a few privileged credentials. Notably, the unusual behaviour was detected by vigilant ANU staff, prompting the removal of the attack from the network. At the time, it was perceived as an isolated incident, rather than indicative of a broader, sustained campaign.
Throughout the campaign, the threat actor displayed a very high level of operational security, frequently covering their tracks and deleting evidence of their actions within the network.
What was exfiltrated from ANU and why did it happen?
The breach of ANU’s network, which was discovered in 2019, was one of the most sophisticated in the history of Australian data breaches. The hackers were able to maintain an advanced persistent threat in the ANU network for five months, and are understood to have accessed 19 years of data covering up to 200,000 former students.
The following personally identifiable information (PII) was in the hacked database:
- Names
- Addresses
- Phone numbers
- Dates of birth
- Emergency contact details
- Tax file numbers
- Payroll information
- Bank account details
- Student academic results
Several theories remain about why the threat actor targeted ANU, even though the primary motivation behind the breach remains a mystery. The actor did not target data in any other high-value areas such as research. One explanation, that has been echoed by several experts, is that the hack was part of a larger operation by a nation-state actor with the intent to gather personal information on high-value targets who were former students at ANU and now hold leadership positions in government and industry.
Regardless of the motivation behind the hack, it remains that it was a severe security breach that has had a lasting impact on the university, its former students and security professionals.
Who was to blame?
Based on the sophistication of the attackers and the type of data targetted, there is a high likelihood that this attack came from a nation-state cyber-espionage team. There is not enough evidence to point the finger at any one country or to completely rule out organised crime. Regardless of who was behind the attack, the vice-chancellor of ANU Brian Schmidt has stated “This was a state-of-the-art hack, carried out by an actor at the very top of their game, at the very cutting edge.”
What did ANU do in response to the hack and how did they recover?
Once the breach was discovered, ANU responded rapidly, with incident response assistance provided by Commonwealth security agencies, IDCARE and Northrop Grumman.
ANU was in the process of upgrading its security following an unsuccessful hack in 2018. Part of this upgrade was a baseline threat-hunting exercise, which was the reason that the attacker was discovered in the system.
As part of their security upgrade, ANU implemented a zero-trust network architecture with the vendor Gigamon which included more than 350 devices. According to Gigamon, these devices “enabled the university to close its visibility gaps and to track activity for any device, network, and traffic type, including East-West traffic. Detailed data from GigaSMART is fed into an asset discovery and cybersecurity automation tool to identify, segment, and enforce compliance of every connected device on the network.”
In their comprehensive public incident report, ANU focused on two lessons in particular: Personally Identifiable Information and Phishing Awareness.
Proceeding on the basis that the data targetted was not fully able to be ascertained, ANU assumed that all data in the compromised systems was at risk. As an initial measure, they had assistance provided to affected members by an Australian non-profit organisation called IDCARE. On the backend, they continued with the implementation of data-safeguarding measures already underway since 2018 and initiated a working group led by the CPO for a full review and development of additional remediation measures.
Based on the number of credentials gained via phishing, ANU has invested in organisation-wide security awareness training. On the backend, they have improved the security of their mail gateway and brought forward the retirement of legacy mail systems.
In addition to the two major lessons, ANU has flagged the following issues for remediation: legacy devices, two-factor authentication, firewall coverage, network hardening, vulnerability and patch management and simulation exercises.
Does the ANU breach of 2019 still have any effects in 2023?
The impact of the breach has lessened since the media coverage of when it was first disclosed in 2019 and because the data has not been publicly leaked to date. It has left a lasting impact on many of the 200,000 potential ex-students and staff who may have had their PII exposed. A colleague of mine is a former student at ANU and is still bothered by the fact that a hostile nation-state threat actor may have their personal information.
When an organisation fails to protect the personal data of its customers, it suffers reputational damage. ANU has worked to repair that damage by expediting its security upgrade project.
Bottom line
In 2019, ANU fell victim to one of the most sophisticated and significant data breaches in Australian history. Threat actors were active in the network for 6 months, potentially accessing the personal information of up to 200,000 people affiliated with the university going back 19 years.
The breach was a major wake-up call to universities and large organisations in Australia that hold personal information. It has made clear the importance of investing in security and having in place multi-layered, defence-in-depth security to safeguard that data.